Finding the network management system that is best fitted for your infrastructure is a significantly crucial task. Fortunately, there’s no scarcity of monitoring and management tools that are capable of offering the vision most network managers require.
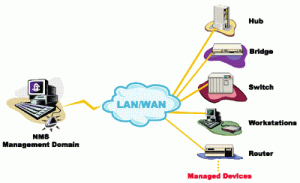 However, to develop the optimum network management base, the IT organization requires to take into account both its legacy environment as well as any latest technologies it plans to install. It is indispensable that systems offer visibility and control over each individual network component, but it is also crucial that they often a clear sight of traffic activity across the network as a whole. IT also requires a control-point from which they can troubleshoot any issues and whenever feasible, issue a mechanized response to solve a problem and limit downtime.
However, to develop the optimum network management base, the IT organization requires to take into account both its legacy environment as well as any latest technologies it plans to install. It is indispensable that systems offer visibility and control over each individual network component, but it is also crucial that they often a clear sight of traffic activity across the network as a whole. IT also requires a control-point from which they can troubleshoot any issues and whenever feasible, issue a mechanized response to solve a problem and limit downtime.
For this function, ventures require a console to act as a combined control point for the network as a whole. IT pros with diverse responsibilities can tap into the console to support their individual functional needs, whatever they’re. Furthermore, these systems must be engineered with a device that can offer a graphical illustration of the network that is based on the user’s precise task.
Whichever route an IT company picks to take to enhance its network management position, it is clear that network managers are require to consider their complete environment. Because each setting is different, each company’s path will vary. Whatever the businesses need is for the network administration platform, it should fit together with their infrastructure to sustain an environment that supplies best performance, proficient resource use and maximum dependability.

 NetFlow is a fixed instrumentation within Cisco IOS Software to distinguish network function. Visibility into the network is a crucial tool for IT pros. In reply to new needs and pressures, network operators are finding it difficult to comprehend how the network is behaving. They need to be aware of these:
NetFlow is a fixed instrumentation within Cisco IOS Software to distinguish network function. Visibility into the network is a crucial tool for IT pros. In reply to new needs and pressures, network operators are finding it difficult to comprehend how the network is behaving. They need to be aware of these: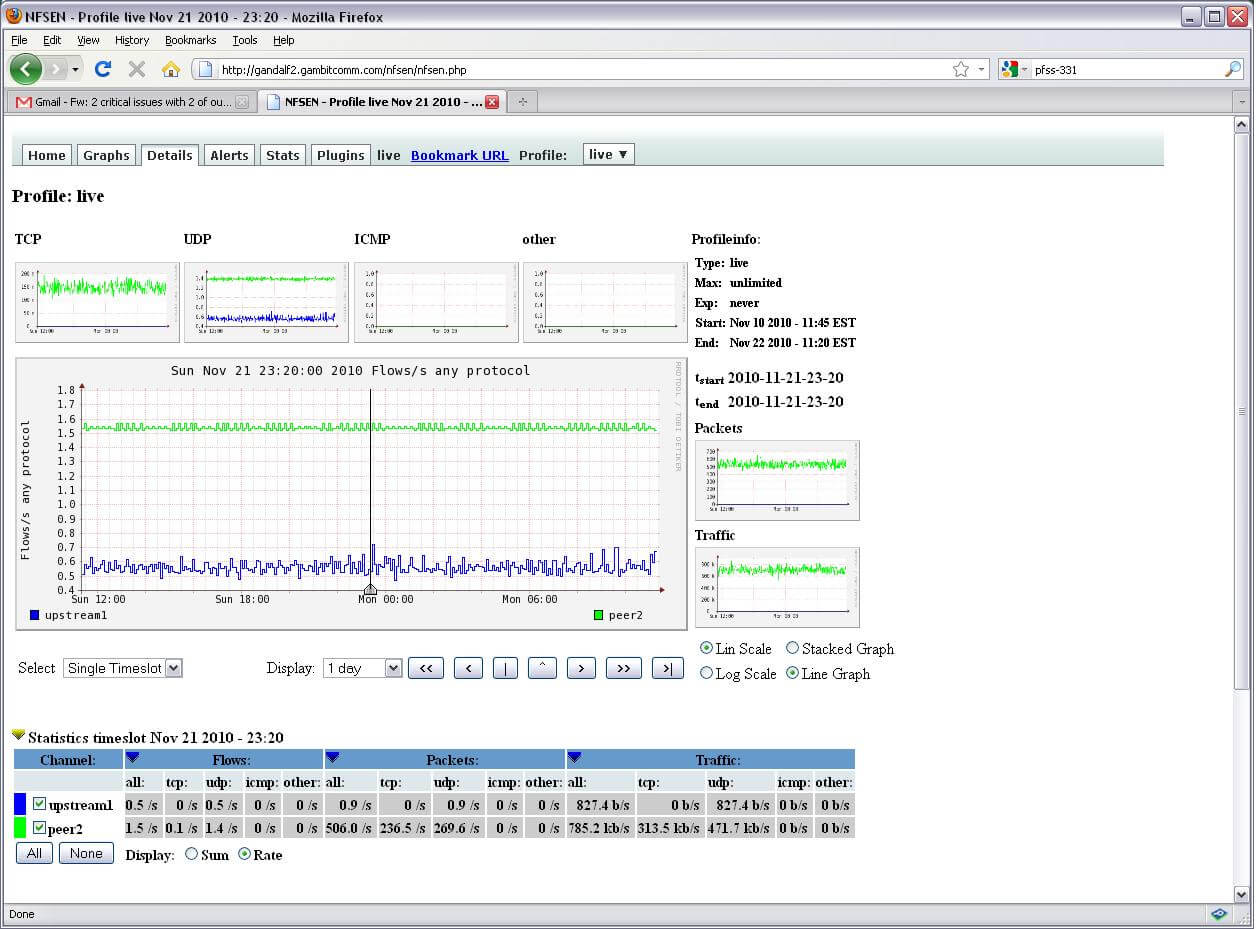 Where NetFlow can be implemented in the network?
Where NetFlow can be implemented in the network?
 • Source IP address
• Source IP address




